Think of your internet and sensitive data like you would a car. We take several preventative measures to keep our vehicles from being the target of thieves. We lock our doors, hide valuables from plain sight, install car alarms and anti-theft devices like the Club, and avoid parking in unsafe and dimly lit areas.
So why don’t we always take similar steps to protect our computers and smart phones from people looking to steal our valuable information or money from our online accounts?
Just like car thieves, most hackers look for easy targets. They’ll prey on victims with weak passwords or who use unsecured WiFi to access important financial accounts or to make online purchases. Fortunately, just like with keeping our cars from getting stolen or broken into, a little cyber defense can go a long way in keeping you from getting hacked.
Below are 5 simple things you can do RIGHT NOW to minimize your chances of being hacked.
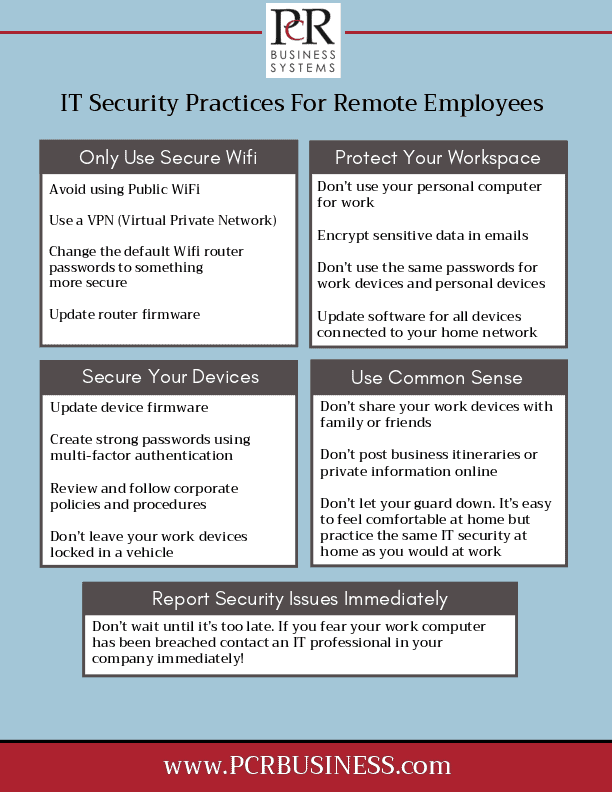
1). Make sure your security software is up-to-date. Don’t ignore those notifications that pop-up on your screen telling you that your operating system requires an update. That update may contain critical security patches that must be installed in order to keep your system protected from hackers.
Email programs, apps and web browsers should all be updated whenever a software update is available. In addition, as we wrote in the article “End of the Road for Windows 7 and Windows Server 2008,” make sure you are using an operating system (OS) that is not obsolete. Using an OS or any software that is no longer supported can leave you extremely vulnerable to a cyber-attack.
2). Create strong passwords, change them regularly, and don’t use the same password for everything. This seems pretty simple, and it is! In the unfortunate event that a hacker gains access to one of your passwords, for example your Facebook login; you can mitigate the damage by ensuring that password is ONLY used for Facebook. If you use the same password for Facebook as you do for your online banking, email, etc. you could be in real trouble as hackers will have access to all of those accounts.
Fortunately, you can prevent hackers from gaining access to any of your accounts by creating strong passwords with a variety of numbers, capital letters, and unique characters, and changing them regularly. Keep a log of your passwords locked in a safe place in your desk or your home.
3). Use Multi-Factor Authentication on all devices. In addition to password protection, you can also thwart off hackers by using multi-factor authentication for all connected devices. Multi-factor authentication simply means that you must present multiple credentials (in addition to just a single password) to gain access to your device or account. Using Multi-factor authentication will help protect your sensitive data against the leading cause of data security breaches– stolen credentials.
4). Install proper antivirus software. If you already have up-to-date security software installed, good for you! You’re one step ahead. If you don’t, make sure you install a firewall today and stay current with updates. Do your research before installing any program or software, and feel free to give us a call at 330.572.7575 or email directly at pat@pcrbusiness.com and we can recommend the best antivirus and antimalware software on the market today.
5). Limit the use of public WiFi and unsecured devices. Do your best to only browse the internet from a secure network. While we understand this may be difficult while traveling, especially if you need to book a last minute hotel or pay a bill online, try to find a network that is safe and password protected. Never use open Wifi for accessing email or important accounts. Just as you wouldn’t leave your purse or laptop on the front seat of your car for a would-be thief to see, you should never display sensitive data on an unsecured network for hackers to get their hands on. Troubleshooting internet connection problems>>
Staying ahead of hackers can be a challenging task. However, implementing these five things today will at the very least make it more difficult for hackers to gain access into your data–limiting the chances they’ll go after you in the first place.
For more information on how you can protect your business from cyber attacks visit us at pcrbusiness.com and check out more posts from our blog.

In Business since, 2004, PCR Business Systems is the leading IT Service Provider in Akron, OH and is SOC 2 Audited and Certified. Schedule a free review of your IT today!