IT Security for Working at Home
Unfortunately, due to the Coronavirus many employees have been forced to work from home, or may be working from home in the near future. If you find yourself in this situation it’s important to remember to follow the best IT security practices when working from home to not put your company at risk of an online virus or cyberattack.
Working remotely can be challenging because you likely don’t have the same security safeguards in place at home as you do in the office. In addition, most people have multiple devices connected to their home Wifi, including personal computers, smartphones, game consoles, etc. These can all offer hackers a gateway into your home Wifi which can then give them a backdoor into the corporate device you are working from. It’s up to you to implement your own layers of security controls at home to prevent your company’s data from being breached.
Cyber criminals love to prey on companies when they are most vulnerable, and one of the weak spots they look for is employees who are not following the best IT security practices for working remotely.
Below is a list of things you can do to prevent cyberattacks while working remotely. You should follow these guidelines whenever you are logged into a corporate laptop or phone, even if it’s just to check a few emails.
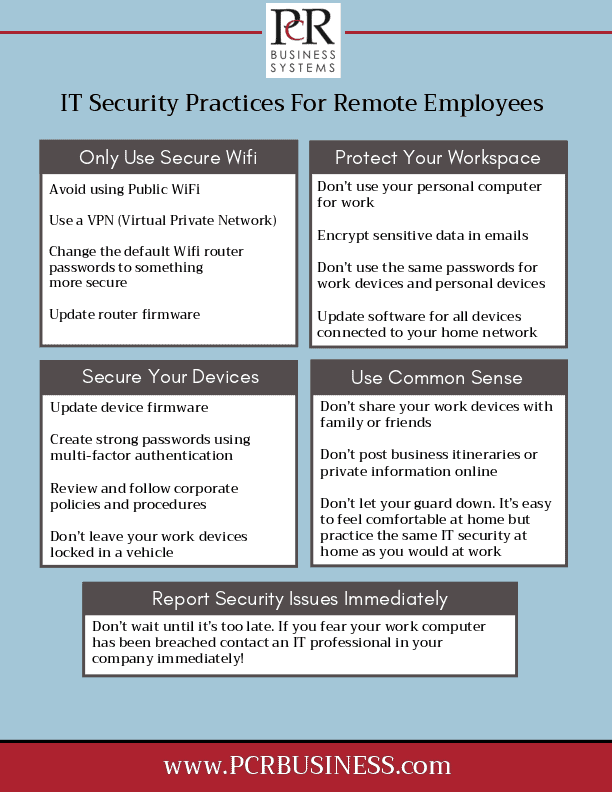
IT Security Checklist for Remote Employees
Only Use Secure Wifi
- Avoid using Public WiFi
- Use a VPN (Virtual Private Network)
- Change the default Wifi router passwords to something more secure
- Update router firmware
Protect Your Workspace
- Don’t use your personal computer for work
- Don’t let anyone eavesdrop on what you are working on
- Encrypt sensitive data in emails
- Don’t use the same passwords on work devices as you do personal devices
- Update software for all devices that are connected to your home network (this includes personal computers, television services, game consoles, thermostats, etc.)
Secure Your Devices
- Update firmware
- Create strong passwords using multi-factor authentication
- Review and follow corporate policies and procedures
- Don’t leave your work devices unaccompanied in a vehicle
- Keep your home or apartment securely locked
Read about having a secure bring your own device policy >>
Use Common Sense
- Don’t share your work devices with family or friends
- Don’t post business itineraries or corporate information online. This includes posting photos that may show addresses, client information, or any other personal or business information in the background
- Don’t let your guard down. It’s easy to feel comfortable at home but practice the same IT security best practices at home as you would at work
Report Any Security Issues Immediately
- Don’t wait until it’s too late. If you fear your work computer has been breached contact an IT professional within your company immediately
Want to learn more about working from home safely? Read about Threat Remediation while working from home >>
Fill out the form below or contact PCR Business Systems if you have any questions about setting up a secure workspace for your remote employees.