My phone rings at four a.m. jolting me from a peaceful dream straight into a panic. I race to answer it. Who’s calling me this early? Something terrible must have happened!
I glance at the screen and see my hometown area code. I don’t recognize the number, but that doesn’t mean it’s not the police or the hospital calling with some awful news.
I reluctantly answer the phone, expecting the worst. “Hello?”
“Your auto insurance is about to expire. Touch seven or stay on the line to speak to…”
I thumb at the hang-up phone icon with rage, not listening to the conclusion of the prerecorded message. I try and fall back to sleep but can’t. My adrenaline is pumping. My heart rate has spiked. I lie in bed wondering what kind of person or business would stoop so low as to spam fellow humans with robocalls.
Telemarketers are bad enough, but at least there’s a real person on the other end of the line that you yell at. Robocalls don’t even give you that satisfaction. Now that I can’t sleep, I lie in bed searching the internet for ways to make these calls stop for good.
Here’s what I found.
According to a call-blocking company called YouMail, approximately 48 billion robocalls were made to Americans in 2018, with even more being placed this year. In October alone, Americans were bombarded with 5.7 billion robocalls stemming from political pitches to fake IRS scams.

Complaints to the FCC and Federal Trade Commission have been pouring in for years topping the list of consumer complaints. In December, the House passed The Pallone-Thune Telephone Robocall Abuse Criminal Enforcement and Deterrence Act, aka the Traced Act— aimed to put an end to robocalls for good.
According to House leaders the new legislation “combats the robocall epidemic by ensuring every call Americans receive will be verified and can be blocked at no extra cost to consumers. It also gives the Federal Communications Commission and law enforcement the authority to quickly go after scammers.”
(Detailed information can be found here).
But will this new law stop those intrusive robocalls from waking us up at night and pestering us during our lunch breaks?
Time will tell, but I’m not going to lose more sleep waiting around to find out. Just as cyber crooks are finding new ways to hack into our networks with ransomware and viruses, the people behind the robocalls will likely do everything they can to scoot around these new regulations and continue to badger us with their scams and bogus offers.
So what can we do to proactively block robocalls and keep us from smashing our new smartphones against the wall? Here are a few tips I found that will hopefully help.
1). Add your number to the FCC’s Do Not Call list by visiting donotcall.gov. According to the FCC, once you add your number, “Telemarketers must remove your numbers from their call lists and stop calling you within 31 days from the date you register.”
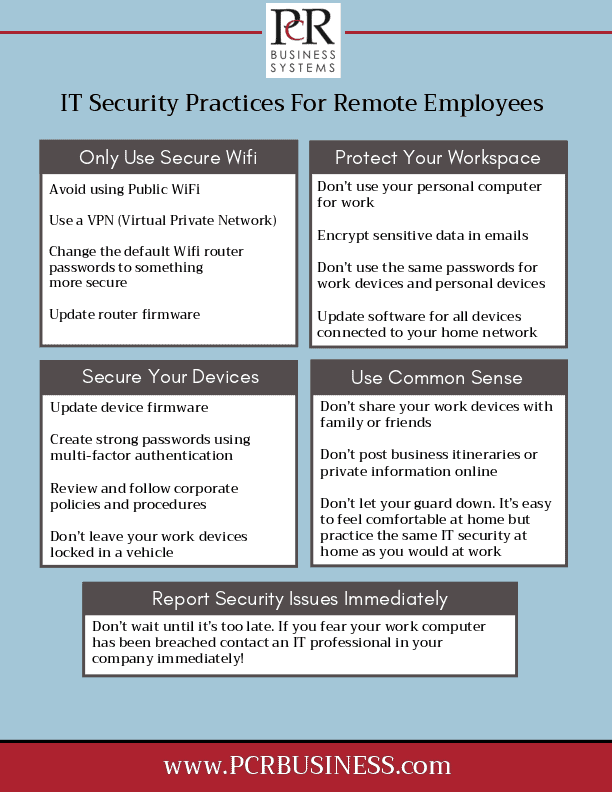
This is the first step I took when doing research for this article. I entered my number on the Do Not Call list, and then waited several minutes before I received a confirmation email. Once the email I arrived I was excited to open it. Could stopping robocalls really be this simple?
Then I read the email stating that I had already registered my phone…back in 2005!
Epic fail, FCC. I must have received over a thousand calls from telemarketers in the past 15 years.
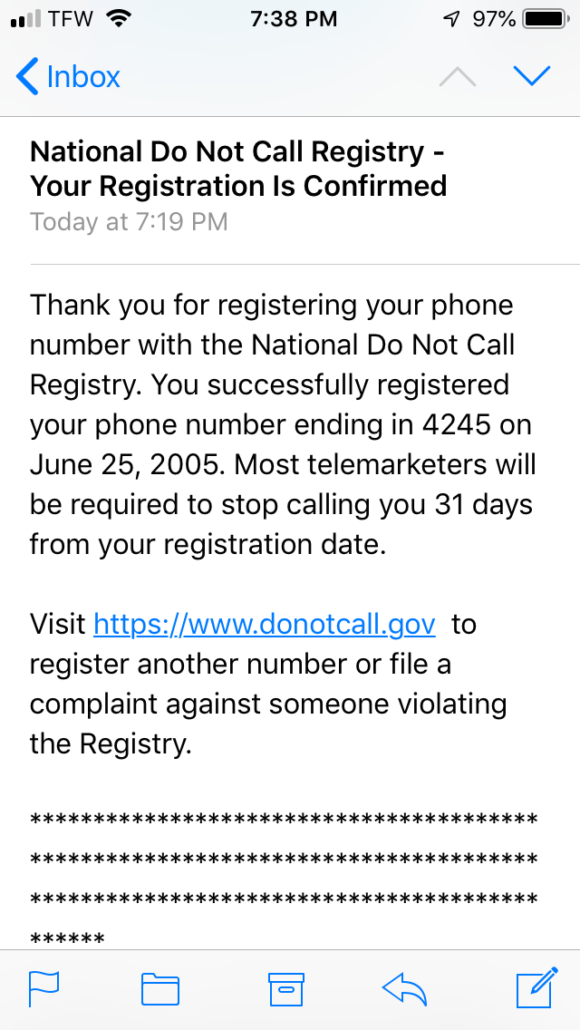
2). Manually block numbers that have come from telemarketers and robocalls. All smartphones have this option. Depending on the type of phone you have the process should be simple. On my iPhone I simply click the information icon to the right of the number, and then scroll down to the bottom and click where it says “Block this Caller.”
Unfortunately, this also hasn’t seemed to stop the problem for me. It has limited it, but the calls have kept coming despite blocking over 150 numbers on my phone.
3) Use a third-party app and utilize your phone’s features. All four major wireless carriers offer some type of call blocking feature to their customers, and most smartphones offer some kind of special blocking tool. For example, Apple’s iOS 13 has an option to “Silence Unknown Callers” which will send unknown numbers directly to your voicemail.
To turn on Silence Unknown Callers, simply go to your iPhone Settings, then Phone, then scroll down and select “Silence Unknown Callers.” It’s that simple.
This is a great option for avoiding robocalls, but be aware, this could also cause you to miss important calls from your doctor or your child’s school. Callers will show up on your recent calls list, but if it’s an emergency, you may not realize they have called in time.
Another step you can take is to download a third-party app to block robocalls. Hiya is a free app for Android and iOS that has received good reviews. Other popular apps you may want to research include Nomorobo (used by Verizon), YouMail, and RoboKiller, just to name a few.
4). Follow the FCC’s best practices to reduce robocalls. These are mostly common sense, but it can’t hurt to remind yourself of these simple rules:
- Ignore calls from blocked, unknown numbers, or numbers you don’t recognize. Note: This includes “spoofed” calls that have the appearance of coming from a local number. I continue to get calls from my hometown area code even though I haven’t lived there in years.
- If a caller or voice message asks you to hit a button to speak with a representative you should immediately hang up. Hitting a button can be a sign to scammers that you are a vulnerable target.
- Do not respond to any questions, especially those that you would answer with a “yes.”
- Never give out any personal information!
- If someone claims to be affiliated with a certain company or government agency, and you have doubts, hang up and double check the number to make sure it is associated with the business or organization they claim to be with.
(Further tips can be found on the FCC website).
5) Trust that the Traced Act will do what it claims. In practice, The TRACED Act would make it a law that phone companies block robocalls free of charge to customers, while also ensuring that calls originate from real numbers.
Let’s hope this is true. In the meantime, it can’t hurt to take a few extra steps on our own to try and stop robocalls from adding unnecessary frustration to our lives.