Are Your Vendors Putting Your Cybersecurity at Risk?

By: PCR Business Systems
Most Northeast Ohio business owners don’t lie awake at night worrying about their vendors’ cybersecurity. You’re too busy keeping your own systems running safely and your clients happy.
Unfortunately, third-party vendors are often the gateway to cyberattacks. If they store your data, connect remotely, or share cloud credentials, your information rides along with theirs. You can have the best firewalls, backups, and passwords in the world, but if one of your vendors gets hacked, your business could still be caught in the fallout.
Crain’s Cleveland recently called vendor cybersecurity “the most overlooked threat” facing Ohio businesses.
And they’re right.
How it Happens
A vendor doesn’t need to be malicious, just sloppy. One lazy shortcut can unravel months of your own cybersecurity work, expose your data, or give hackers the keys to your systems.
A few possible scenarios include:
- A bookkeeping firm’s laptop gets stolen, exposing client data.
- A marketing vendor uses a weak password on your shared files.
- A tech contractor skips multi-factor authentication on remote access.
In addition to putting your business at risk, cyber liability insurance providers and auditors will want to make sure that your vendors are protecting your data. They want evidence, not promises. That’s why “trust but verify” isn’t just a saying anymore. It’s a policy.
What You Can Do to Mitigate Vendor Risk
Almost every business in Northeast Ohio relies on outsourced IT vendors, such as IT providers like PCR Business Systems, software providers, hardware integrators, and more. That’s why it’s so important to make sure your third-party vendors have the highest level of security controls in place to not only protect their systems, but also yours.
You can’t assume their cybersecurity standards match yours. And if they’re careless with your data, the damage doesn’t stop with them. It lands squarely on your desk.
The first place to start is by only working with SOC audited vendors. A SOC audit (short for Service Organization Control) is an independent review that verifies a company is following strict cybersecurity, privacy, and operational standards.
PCR Business Systems: SOC Audited MSP
Several years ago, we made the decision to go through the SOC 2 audit process, one of the most rigorous security standards in our industry. It wasn’t quick or cheap, but it was worth every bit of time and effort.
We wanted our clients to know, without question, that their data and systems are protected by a partner that meets the highest level of verified security controls.
Since then, we’ve completed the SOC 2 Type 2 audit every year, which means an independent auditor reviews and tests our security practices from top to bottom, not just policies on paper, but how we actually operate day to day.
It’s our way of proving that when we say we take cybersecurity seriously, we have the evidence to back it up.
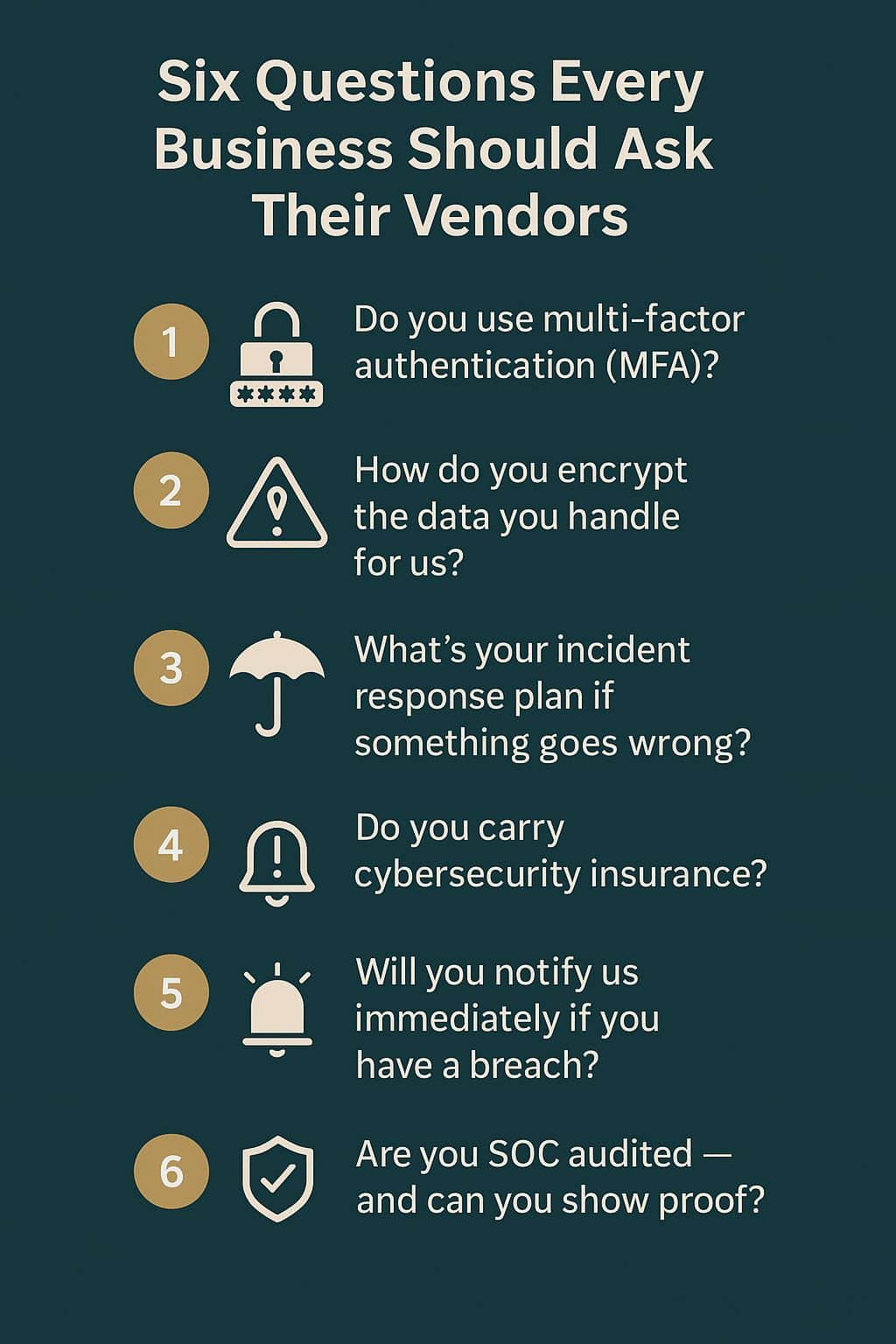
Six Questions Every Business Should Ask Their Vendors
The next step is conducting your own audit to make sure your third-party vendors aren’t being lazy with their cybersecurity. Here are six simple questions you can ask:
- Do you use multi-factor authentication (MFA)?
- How do you encrypt the data you handle for us?
- What’s your incident response plan if something goes wrong?
- Do you carry cybersecurity insurance?
- Will you notify us immediately if you have a breach?
- Are you SOC audited — and can you show proof?
You can’t control every vendor you work with. But you can control who you trust and how you verify they take cybersecurity seriously. Start asking those six questions. Especially the last one. Schedule a quick call with PCR President Pat Carroll to learn more.




