The Top Reasons Cyber Liability Claims Get Denied
And how to make sure your cyber insurance provider pays up.

By: PCR Business Systems
Picture this. It’s a Wednesday morning. Your operations manager can’t log in. Invoices won’t load. The ERP is frozen. Within minutes, you realize this isn’t a glitch, it’s ransomware.
You remember your cyber liability policy, the one you dutifully renewed last year. “We’re covered,” you tell yourself. But when you call the carrier, they ask for proof of multi-factor authentication on every account, records of backup testing, and evidence of employee phishing training.
Your stomach sinks. You have most of it, but not all.
And that’s when the adjuster says the words no business owner ever wants to hear: “We can’t approve your claim.”
The Hard Truth About Cyber Insurance
When insurers first rolled out cyber liability policies, they paid out more freely. But after billions in ransomware losses, the rules changed. Now, they expect proof that you’ve done your part in making sure you have the highest cybersecurity controls in place. If they can’t see that proof, they can deny your claim. We see it happen every day right here in Northeast Ohio.
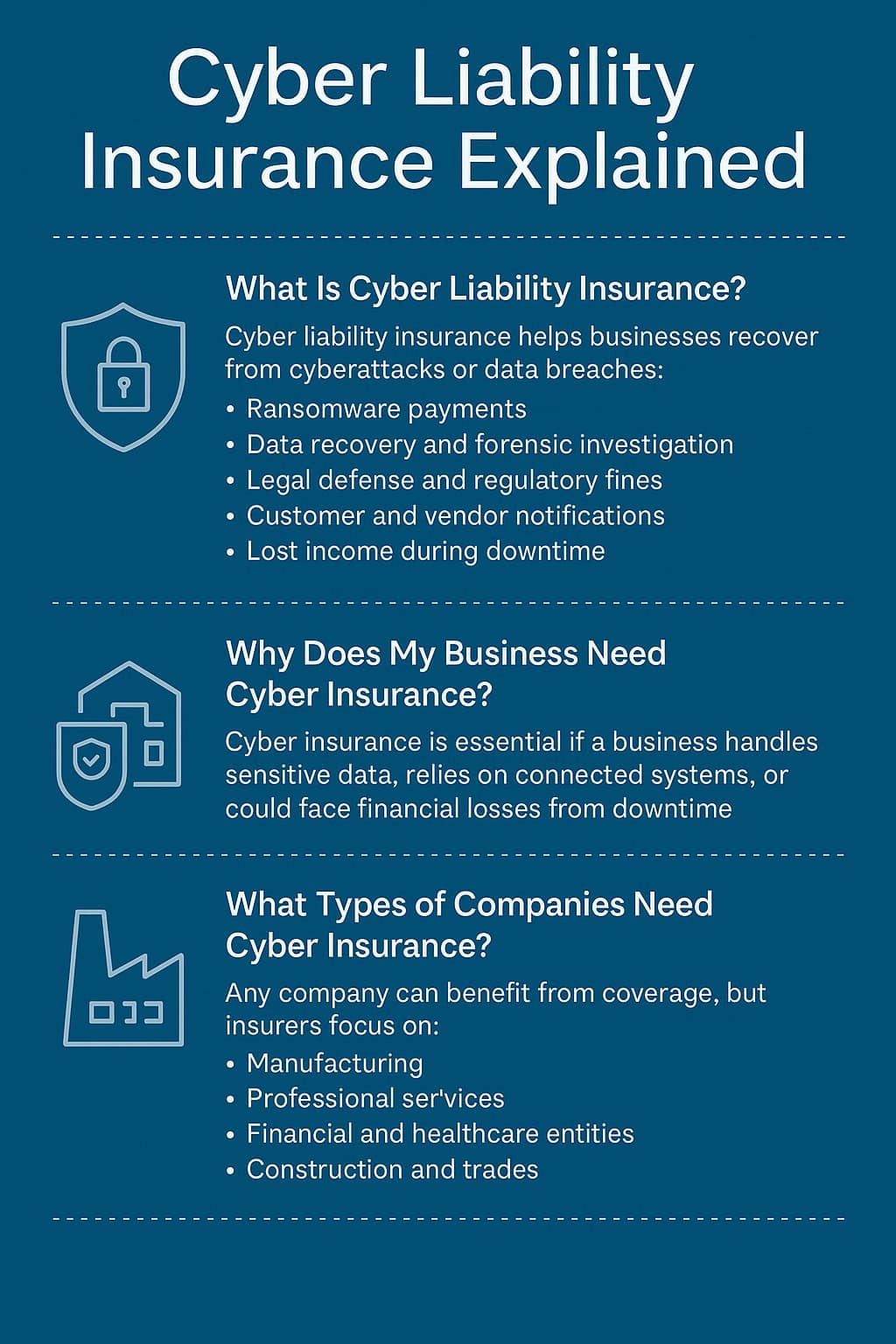
The Top 3 Reasons Cyber Claims Get Denied
1. You “checked yes” on controls you can’t prove
Most renewal forms ask, “Do you use multi-factor authentication on all accounts?” Many companies mean to say “mostly.” The insurer hears “always.”
That tiny difference becomes a six-figure argument later.
2. Backups that don’t actually restore
We’ve seen it too often, backups humming along for months, quietly failing in the background. When the ransom notes hit, the restore fails. The insurer calls that “failure to maintain controls.”
3. No evidence of training or testing
You might have sent out phishing tests once. But insurers want ongoing user training and documented results. If your users keep clicking malicious links, they can classify it as “untrained negligence.”
How to Make Sure Your Claim Holds Up When It Matters
Insurance companies trust documentation, not intentions. So your best move isn’t buying more coverage, it’s making your business provably compliant. Here’s what you can do:
Step 1: Turn your IT into evidence
Every month, ask your IT team or provider to show:
- MFA coverage reports
- Patch compliance logs
- Backup success and restore times
- Endpoint protection status
- Phishing test results
Put those in a single folder — your “insurance evidence kit.” If you ever face an incident, that kit could be worth more than your policy itself.
Step 2: Test, don’t trust
Schedule quarterly backup tests and policy reviews. Make them part of your culture.
Step 3: Align your IT partner with your insurer
Your managed IT or co-managed cybersecurity provider should know exactly what your carrier expects. If they can’t produce evidence reports or compliance artifacts on demand, it’s time to ask tougher questions. Your IT team should be your first line of defense and your insurance advocate.
Cyber insurance isn’t just for the big players. Small manufacturers, nonprofits, and accounting offices are being targeted precisely because hackers know they often don’t have the necessary security controls in place. Too often, SMB’s think “it won’t happen to us.”
Unfortunately, the question isn’t if you’ll face an incident, it’s how ready you’ll be when it happens, and whether you have cyber liability insurance and if your insurer will stand with you or walk away.
Schedule a meeting with PCR President Pat Carroll make sure your Ohio business has the cybersecurity controls, staff training, and documentation in place to file a successful cyber liability claim should a breach occur.




